[ This is a reposting of my teaching blog post previously hosted on http://users.ox.ac.uk/~coml0454.
NOTE: I no longer teach at University of Oxford and this is a description of how I used to teach the course.]
Summary
This post describes how I use virtual machines to create exercises and assignments for the course I teach. The post also shows how the distribution of the virtual machines to the students allows them to take the skills they have learned in class away with them.
Background
I teach the forensics (FOR) module on the Software and Systems Security programme. The week-long module includes a number of classroom exercises associated with the extraction and analysis of computer system artifacts. The assignments may also involve the extraction and analysis of computer system artifacts. To encourage understanding of the extraction and analysis process the exercises use Linux and Sleuthkit utilities which are run from the command line. To allow the transfer of understanding and skills from the classroom exercises to the assignment, the students use a Linux-based VM for the classroom exercises and receive a copy of that VM for use when undertaking the assignment.
The FOR Module
Since 2009 I have been a visiting lecturer teaching computer forensics at University of Oxford in the UK on the part-time Software & System Security Masters and the Software Engineering Masters programmes in the Department of Computer Science. These are not online programmes. The students must attend a week-long classroom teaching session at the university. After the teaching week the students have six weeks to complete an assignment at home, away from the university. The FOR module is systems focused and covers the aspects associated with the forensic analysis of: computers; networks; mobile; cloud computing; industrial systems.
The Computing System
The characteristics of any computing system are determined by three elements:
- The architecture of the hardware used to physically realize the system;
- The operating system run on the hardware that provides the services and interfaces to the hardware;
- The (compilers used to create the) applications that run on the system.
An understanding of the interrelationship of these elements provides a greater insight into the behaviour of a computer system. This view comes from having sat in on the Compilers, Operating Systems and Architectures course taught in the Computer Science Dept at University of Wales Swansea in the mid-1980s.
Issues
The students taking the FOR module have a week of classroom-based teaching. During this time they undertake a number of computer-based exercises. I want to provide a mechanism that provides the classroom experience to the students outside the classroom when they are working on the assignment.
Classroom contact time is valuable. I want to focus on teaching. I don’t want to use contact time dealing with forensic tool installation.
There are potential license issues distributing Mac & Windows operating systems and applications so I want to use GNU Linux distributions with open source applications.
Education
Students learn through:
- hearing;
- seeing;
- doing.
The act of doing forensic analysis helps to reenforce the theory and ideas that the students hear and see. The exercises are an important aspect of the teaching as they provide the students with the experience of doing the forensic analysis with various tools before they leave the classroom environment.
Tools For Doing
To encourage understanding of the forensic extraction and analysis process the exercises use Linux and Sleuthkit utilities which are run from the command line. During the FOR module the students use:
- GNU command line utilities - dd, nc, sfdisk, fdisk, grep, mount, md5sum, sha1sum, file, xxd, ls, find, cat, less, more, strings
- Sleuthkit
- Wireshark
The command line utilities and Sleuthkit allow the students to gain a clearer understanding of the relationship between the computer hardware architecture and the operating system, especially with respect to the file system.
Teaching Use Cases
There are three main use cases for the use of virtual machines in my teaching:
- Preinstalled with the tools used to analyse evidence for use by students in the classroom and by me when creating model answers;
- Creation and preparation of assignment evidence;
- Distribution to students for use on the assignment.
Lubuntu VM Preinstalled With Forensic Tools Use Case
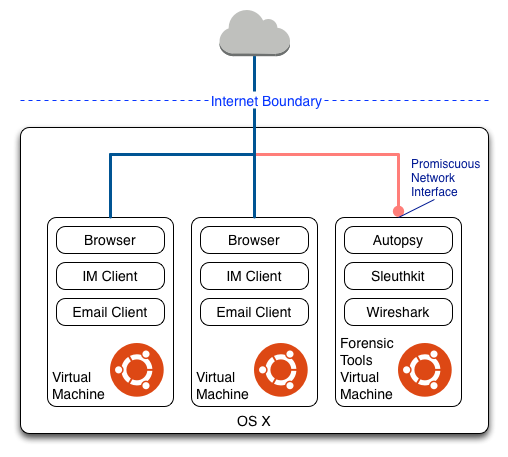
I have created a Forensic Tools VM which is preinstalled with the command line utilities and Sleuthkit. I also install Wireshark and Autopsy. Details on how to create the Forensic Tools VM can be found here. This VM is used in the classroom by the students to perform the exercises. The VM can also be used to conduct the assignment. I use this VM when I create the model answers for the exercises and assignment to ensure the VM functions correctly and is capable of supporting the analysis.
Creation And Preparation Of Assignment Evidence Use Case
One of the issues when creating examples of forensic evidence is coming up with suitable quantities of reasonable examples of communication and interaction between people. I draw on open source materials to achieve this when possible. For example a recent assignment involved four characters:
- Samuel Pepys. He lived in London in the 17th Century and keep a diary. He worked in King Charles’ Navy Office;
- John Evelyn was a friend of Pepys’ and they corresponded;
- Alexandrine de Rye was linked to a spy network in the 17th Century;
- Elizabeth Queen of Bohemia had a link to the British Royal Family during the 17th Century.
I used material from Samuel Pepys’ diary and his correspondence as the basis for blog posts and emails respectively.
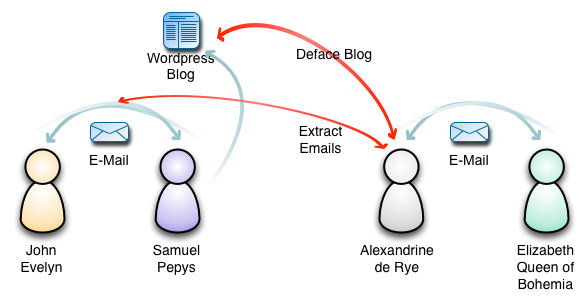
Using Virtual Machines To Create Assignment Evidence
The other issue when creating an assignment is implementing the scenario with sufficient fidelity to provide a rich set of evidence. Virtual machines readily allow a comprehensive set of infrastructure to be setup to implement the scenario. Using the scenario detailed above as an example, two virtual machine were created. One was a server used by Samuel Pepys and John Evelyn to exchange emails and to host Pepys’ Wordpress blog. The server was accessible from the Internet by port forwarding through the network firewall and using a DynDNS domain. The other VM represented the computer used by Alexandrine de Rye for her hacking. This VM connected to the Internet through a VPN tunnel with an end point in the Netherlands. Elizabeth Queen of Bohemia and Alexandrine de Rye exchanged emails using an Internet-based email server.
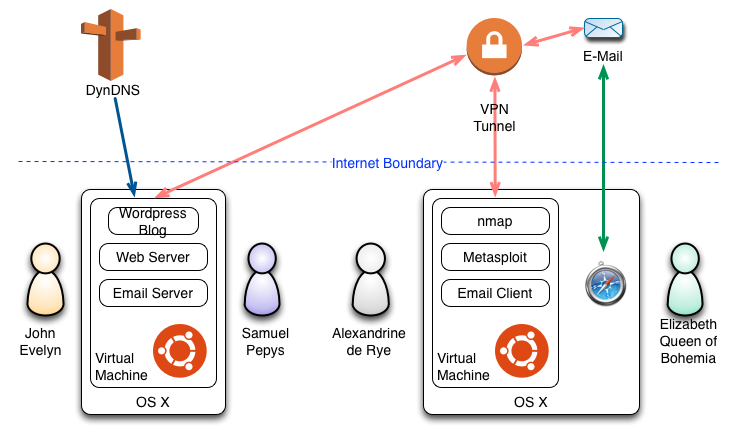
I use VMware Fusion Professional (v5) so that the VMs can be used with VMware Player, VMware Fusion or VMware Workstation. I keep the compatibility low so that the students can use older versions of VMware with the VMs and they don’t need the latest version.
Evidence Capture & Analysis
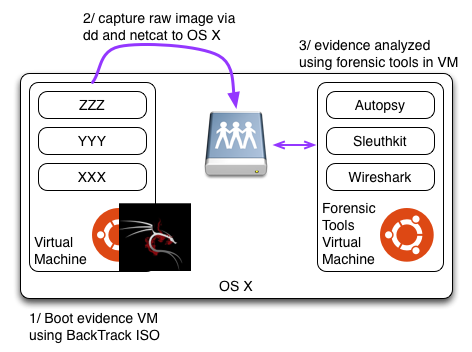
Each VM was imaged. The VMs are imaged by booting the VM using Kali (formerly BackTrack) then using dd and nc to stream the raw disk volume to the host Mac. The raw images stored on the Mac are then accessed by the Forensic Tools VM through folder sharing. The server image was used for one assignment. The hacker’s image was used for a second assignment.
Capture of Network-based Evidence
The evidence captured for the assignment described above was images of the virtual machine disks. Network-based evidence is another type of evidence that can be used in forensic investigations. By using virtual machines to create evidence for exercises and assignments, network-based evidence can be easily captured. One or more virtual machines can be run to generate disk and network-based evidence on a host system. An additional virtual machine is run with the forensic tools including Wireshark. Wireshark is run to collect network traffic from the forensic tools virtual machine’s network interface which is in promiscuous mode. The captured NBE can then be saved on the host.
VM & Evidence Distribution Use Case
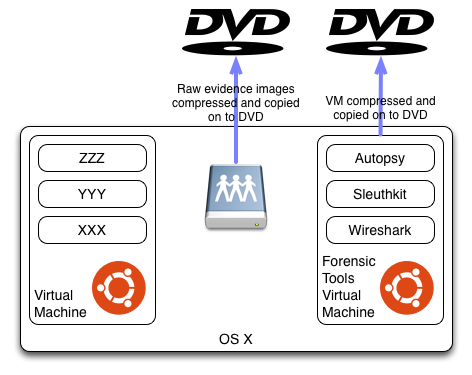
To distribute the evidence and the forensic tools VM for the assignments, the files are compressed and copied on to DVDs. Using DVDs limits the potential size of the forensic tools VM and the evidence partitions. I try to ensure the compressed VM and evidence images are less than 4 GB each. As a consequence I have started using Lubuntu for the latest VMs. Lubuntu uses a lightweight window manager and does not have the Open Office application suite in the distribution so the resultant VM and evidence images are smaller than when Ubuntu is used.
Conclusions
Using virtualisation to support my teaching on the FOR module allows me to:
- Distribute a pre-formed sets of tools to the students so that the skills and experience they gain in the classroom can be reused outside of the classroom;
- Create complex scenarios, involving multiple computers, for assignments;
- Create a pre-formed set of tools that alleviate issues associated with installing forensic tools on the classroom computers;
- Distribute GNU Linux operating system and applications that can be run on any host operating system overcoming the licence issues associated with the distribution of Mac and Windows software.
Acknowledgements
Phil Gyford for the The Diary Of Samuel Pepys website.
Dr. Nadine Akkerman for her blog post on the “Ciphers and Codes in the Letters of Female Spies”.